AWS services — Identity Access Management (IAM)
A high-level overview of the AWS service IAM

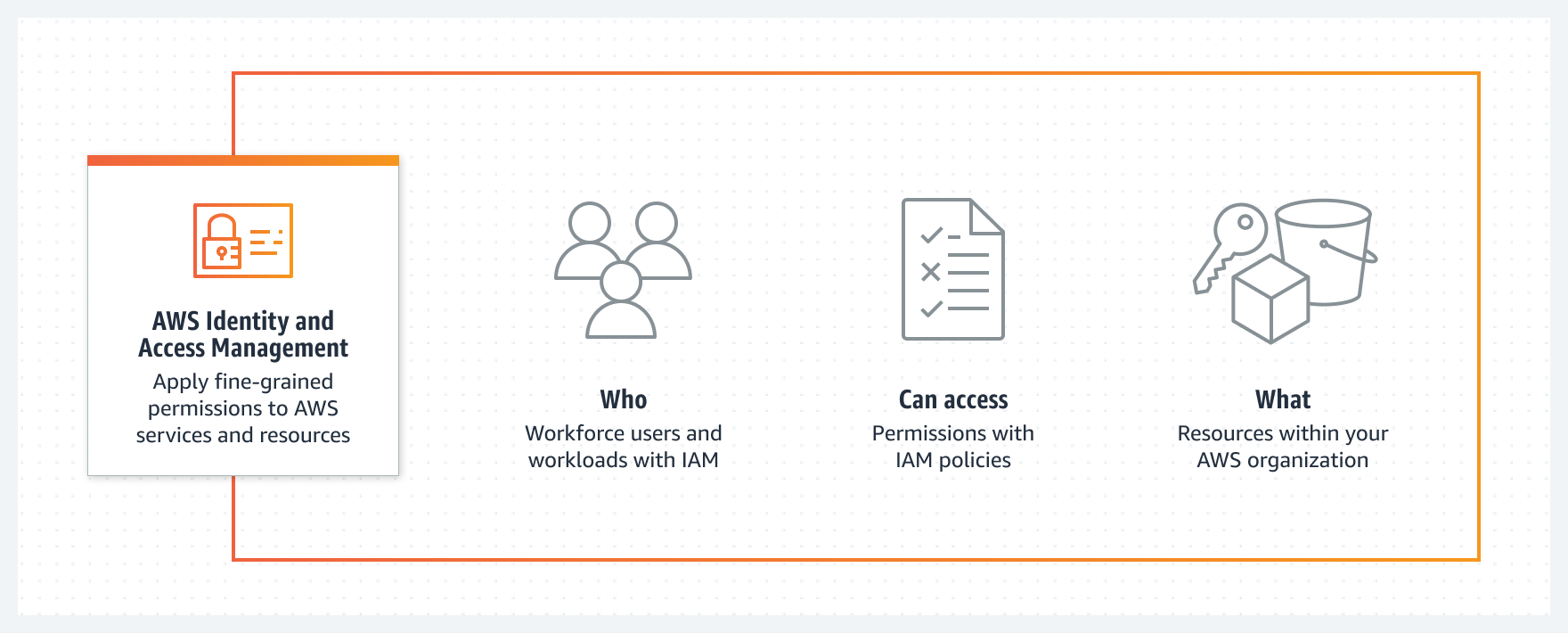
In this blog post, we are going to take a look at one of the most important and most used AWS services — IAM. It allows for securely managing identities and providing access to AWS services and resources.
How does it work?
With AWS — Identity and Access Management (IAM), you can specify who or what can access services and resources in AWS by using the following components.
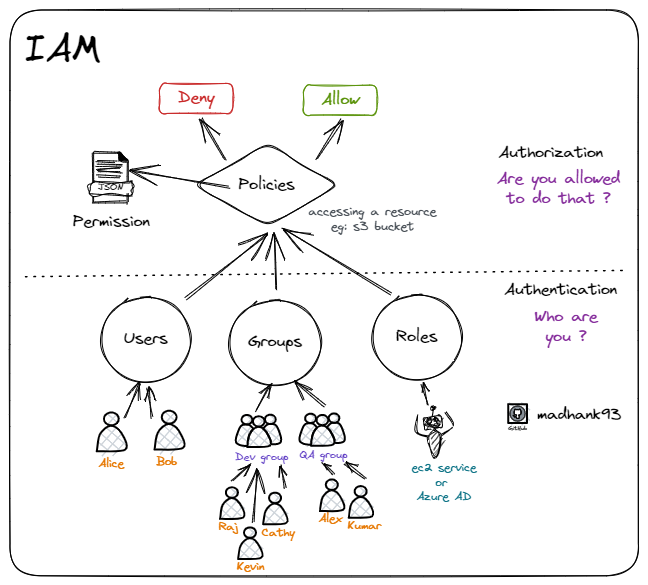
1. Users:
Users represent individual entities (like people, applications, or services within AWS) that can interact with your AWS resources like EC2 instances or S3 buckets. Each user is assigned a unique username and access credentials (password or access keys) for authentication.
2. Groups:
Groups are collections of users (eg: Dev group or QA group). Assigning permissions to groups makes it easier than managing access for multiple users with similar roles or responsibilities. This simplifies the process of granting and revoking permissions across multiple users.
3. Roles:
Roles are similar to users, but they are not associated with a specific identity. Instead, roles are assumed by resources, such as EC2 instances, Lambda functions, EKS cluster, or applications running on Azure. This enables these resources to access other AWS services securely without needing long-term credentials.
4. Permissions:
Permissions define what actions are allowed or denied to access AWS resources. By default, all the permissions are denied. Permissions are managed through policies, which are JSON documents that outline the permissions in a structured way. Policies can be attached to users, groups, and roles.
Permission Name: ListBucketObjects
Action: s3:ListBucket
Resource: arn:aws:s3:::my-bucket
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::my-bucket"
}
]
}
5. Policies:
A policy is a document that defines permissions in a granular manner. AWS provides managed policies that cover common use cases, and custom policies also can be created. Policies can be attached at various levels (user, group, role, or resource) to control access.
One of the main advantage of using IAM services is helping us to grant least privilege access or granting only the permissions required to perform a task
Originally published on Medium
Reference: